I have been thinking about self-hosting my personal photos on my linux server. After the recent backdoor was detected I’m more hesitant to do so especially because i’m no security expert and don’t have the time and knowledge to audit my server. All I’ve done so far is disabling password logins and changing the ssh port. I’m wondering if there are more backdoors and if new ones are made I can’t respond in time. Appreciate your thoughts on this for an ordinary user.
There probably are, there’s a reason why super high security systems aim for airgapping of sorts, and even that’s not immune.
I’m pretty sure most closed source software is already backdoored.
It’s a feature!
That’s the neat part, we don’t!
…but, we at least can have a shot of finding them.
In the meantime, I’d advise you to keep an eye out and maybe look into threat models. As people said in this thread already, bad actors probably don’t care about your personal photos.
Unless OP is a celebrity or politician. Or knows they have an enemy with the resources to find and exploit potential backdoors.
Self hosting personal photos doesn’t generally require opening anything up to the internet, so most backdoors would not be accessible by anyone but you.
Or someone who has penetrated your network.
Of which the chances are slim to none for 99% of people simply because they aren’t interesting enough to be a target beyond phishing, scans, and broad attacks.
That’s the neat part, you don’t. However if you stay up to date it is not a big deal.
Well not too up to date as we just have witnessed 😁
Just use a stable system
We don’t know. However, no one cares about your personal photos ; no one will ever attempt to hack you specifically unless you’re a high value target (in which case, stop hosting your photos anywhere immediately)
The only thing that could get your photos is if an undiscovered backdoor is exploited by someone doing some sort of a mass attack. As far as I know, they’re pretty rare, because people with the means to do them generally have a specific set of people they care about (which you are unlikely to be a part of).
unfortunately, mass attacks happen all the time. if you ever had access to the authentication logs of an SSH server with an unfirewalled port 22 into the internet that has been running for a few months, you would see international IPs starting port scans and brute force attacks. there is always someone out there trying to hack random IPs. it’s fucking wild west out there.
Yeah. I’d recommend using ssh keys and disabling password authentication whenever something is exposed to a public network
We don’t know. However, no one cares about your personal photos ; no one will ever attempt to hack you specifically unless you’re a high value target (in which case, stop hosting your photos anywhere immediately)
To those assumptions I would say : we don’t know. Personal vendettas do exist and we cannot look into the minds of individuals going crazy neither.
That fair enough I guess, really depends on what kinda personal photos you have. I know people are worried about revenge porn, I personally think the only actual remedy is not having any porn of yourself anywhere unless it’s your job 🤷🏻♀️
no one will ever attempt to hack you
My brother in Christ, how do you think botnets get built?
They did say specifically. I think bothers are usually automated attacks.
We don’t know. But if there were well known backdoors to mainstream security practices we might see more companies that depend on security shutting down, or at least shutting down their online activities. Banks, stock trading, crypto exchanges, other enterprises that handle money, where hacking would be lucrative.
There’s a concept of acceptable levels of risk. Companies are not going to shut down out of fear, or miss out on the business opportunities of online presence. There’s money to be made.
Even with things as serious as spectre allowing full dumping of CPU and RAM contents simply by loading a website, I can’t think of a single company that just said “well shit, better just die”.
Serious, potentially business ending, security issues usually have a huge amount of effort when discovered put into mitigations and fixes. Mitigations are usually enough in the immediate “oh shit” phase. Defense in depth is standard practice.
I don’t think you need to worry about backdoors with most of those. Worry more about unfixed security holes due to an extreme emphasis on “stability” as in using old versions when fixes have already been released when it comes to anything hosted by large companies.
“We don’t” is the short answer. It’s unfortunate, but true.
Good question. I have asking myself the same thing as well. In case of ssh it is possible to use 2FA with a security key, which is something I’d like to put in my todo.txt
You don’t. Hackers often exploit things like this for ages before they are found. Every bit of non simple software also has bugs.
But chances are you won’t be the target.
Just keep everything updated and you should be alright.
And implement least privilege and automatic updates
As many have pointed out, you don’t know that there is not a back door in your software.
One way to defend against such an unknown is to have a method of quickly reinstalling your system, so if you ever suspect you have been compromised you can reload your OS from scratch and reconfigure it with minimal fuss. This is one reason I recommend folks learn one of the configuration management systems like ansible or puppet, and use those to configure your Linux servers. Having config management also helps you recover anfter unexpected hardware failures.
Defense is done in layers. No one layer will protect you 100%. Build up several layers that you trust and understand.
Very good points. Call me paranoid but i always fear I might fail to notice the symptoms of something nasty going on. I wish linux had a built-in, easy-to-use auditing/alerting system. I know this can be achived by experts but others have no idea what’s actually going on on their machines.
Dude, you’re so not paranoid. This stuff has happened to me. I had a Wordpress blog that was hacked and the exploit was stored in the DB so even after reloading the OS I still was infected because I hadn’t sanitized my database. Luckily it was just Google search viagra spam, and it was a valuable lesson.
you don’t and will never will. I would recommend reading a lecture by Ken Thompson the co-creator of Unix for more details on this https://www.cs.cmu.edu/~rdriley/487/papers/Thompson_1984_ReflectionsonTrustingTrust.pdf
The main solace you can take is how quickly xz was caught: there is a lot of diverse scrutiny on it.
The thing is there are a few thousand of those people
Maybe millions of potential eyes, but all of them are looking at other things! Heartbleed existed for two years before being noticed, and OpenSSL must have enormously more scrutiny than small projects like xz.
I am very pro open source and this investigation would’ve been virtually impossible on Windows or Mac, but the many-eyes argument always struck me as more theoretical/optimistic than realistic.
Heartbleed existed for two years before being noticed
That’s a different scenario. That was an inadvertently introduced bug, not a deliberately installed backdoor. So the bad guys didn’t have two years to exploit it because they didn’t know about it either.
It’s also not new that very old bugs get discovered. Just a few years ago a 24 year old bug was discovered in the Linux kernel.
And are bugs harder to find than carefully hidden backdoors? No-one noticed the code being added and if it hadn’t have had a performance penalty then it probably wouldn’t have been discovered for a very long time, if ever.
The flip side to open-source is that bad actors could have reviewed the code, discovered Heartbleed and been quietly exploiting it without anyone knowing. Government agencies and criminal groups are known to horde zero-days.
Call me names… But sometimes the story has far more branched backstories than they actually shed into light.
Trust nobody, not even yourself.
You never know what security holes exist until they’re exploited. Nothing you can really do about that. Security and convenience have always, and will always, be a trade off and a matter of personal acceptability. If you host anything, it will be potentially vulnerable, way less so if you take proper precautions. If you’re not just overtly insecure, you’ll probably be fine, but there’s no way to say for sure.
Reading the source code for everything running on your machine and then never updating is the only way to be absolutely 100% sure.
Even with that you will miss something
This is a sliver of one patch, there is a bug here that disabled a build tool that breaks the attack. Can you find it?
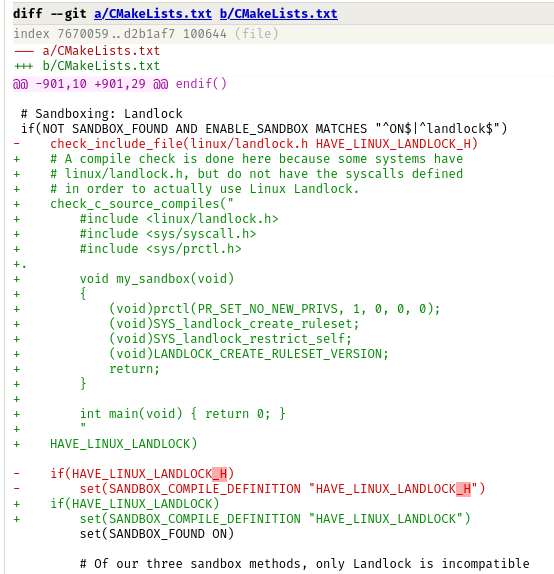
hint
It is one singular character. Everything else is fine.
Solution
It’s the dot on line 9












